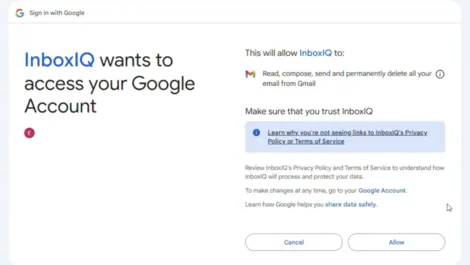
Cloud security encompasses the technologies, policies, controls, and services that protect cloud computing environments, data, applications, and infrastructure from cyber threats. As businesses increasingly adopt cloud platforms for scalability and flexibility, securing these environments has become critical to safeguard sensitive data and maintain compliance.
The recent stories highlight a dynamic landscape marked by advancements in privileged access controls, zero trust architectures, AI-driven threat detection, and collaborations among leading cybersecurity firms. Readers will find insights into emerging threats such as ransomware targeting cloud workloads, the rise of generative AI increasing security risks, and the importance of integrating multi-cloud security tools.
By exploring these developments, readers can learn best practices for cloud server privilege management, understand challenges in hybrid and multicloud deployments, and discover how innovations in AI and automation are shaping the future of cloud security. This collection also emphasizes the significance of visibility, control, and identity management in mitigating evolving threats within cloud environments.
Whether you are looking to enhance your organization's cloud security posture or seeking to stay informed on the latest trends and technologies, this tag provides valuable perspectives and actionable strategies to navigate the complexities of modern cloud security.